In this article, we will look at the definition of SBC to consider the role and function of SBC or Session Border Controller as one of the essential elements of telephone and telecommunication systems.
The proliferation of VoIP-based telephone services has made it vital to prevent cyberattacks, control signaling and audio (media) at the edge of the network, and secure the network.
What is SBC or Session Border Controller?
Before defining SBC, it is essential to understand the potential dangers of telephone and telecommunications systems.
In general, the risks of VoIP-based telephone systems can be divided into the following three categories:
1- Extortion: In this type of attack, hackers try to disable the VoIP system by sending large amounts of requests (packets) and suddenly loading the VoIP system. These attacks include:
DOS / DDOS attacks
Registration Floods or sending large amounts of Registration requests
Malformed SIP Headers or sending incomplete Sip Headers
Call floods or sending a large number of short call requests to establish and produce multiple sessions
2- Intrusion: In this type of attack, hackers try to disable VoIP systems through operations such as Brute Force, Call Server, or other components. These attacks are also called phishing attacks, in which the target of hackers is to extract network information, personal account information, passwords, and so on. Therefore, the target of these attacks can be divided into the following two categories:
Network Scanning
Account Hacking
3- Theft of Services: Hackers use your VoIP and SIP Trunk system to make calls, especially external calls, which causes high costs to the organization.
Issues such as DDOS attacks, Brute Force, etc., will cause various problems in the network, highlighting the need for an element that can protect the telephone system against these attacks; This critical element is called the SBC or Session Border Controller.
Now that we know the potential dangers of VoIP systems let’s look at SBC.
SBC stands for Session Border Controller as a kind of Firewall, located at the edge of networks (VoIP) wherever the two sides of the SIP message are involved, the task of protecting and increasing the security of VoIP telephone systems (VoIP) against various attacks is in charge. SBC is not a firewall, and there are many differences in the two’s role and function.
SBC is an element in VoIP systems, and a Firewall is a protection element in computer networks. SIP messages and packets used in VoIP systems also carry RTP content with them, and firewalls cannot examine the nature of SIP packets and how they relate to RTP streams. In other words, in practice, the Firewall does nothing but perform some network actions, such as activating/deactivating the port in the field of VoIP.
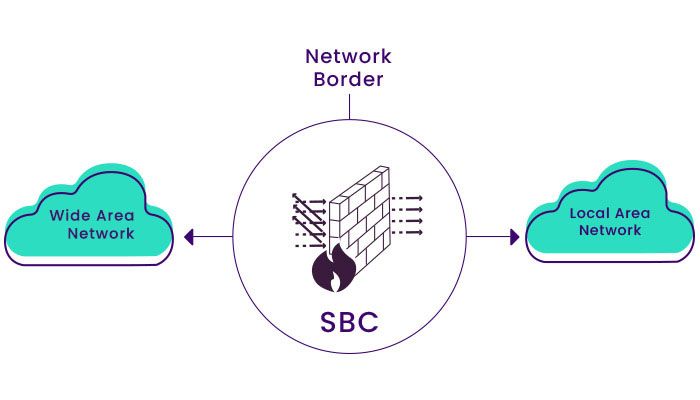
What are the tasks of SBC?
SBC has the task of protecting them in VIP systems and performs security cases in different ways, which we will summarize in the following:
• Topology Hiding: This feature provides a mechanism that prevents IP visibility and communication between the VoIP system’s internal nodes. This mechanism is called Back to Back User Agent B2BUA, which means that all requests reach the SBC, and if the SBC approves them as an Agent, it sends the requests to the SIP request nodes.
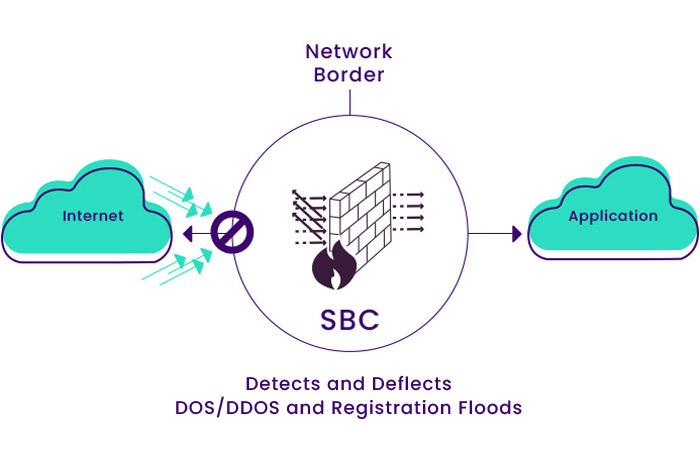
• Detect and prevent DOS / DDOS attacks: In this type of attack, hackers send thousands of requests to the Registry or SIP Headers, incomplete, etc., by robots from different or identical sources to pressure the system and cause disruption. The task of the SBC is to detect such attacks and determine the specific limit for receiving packets from a particular source.
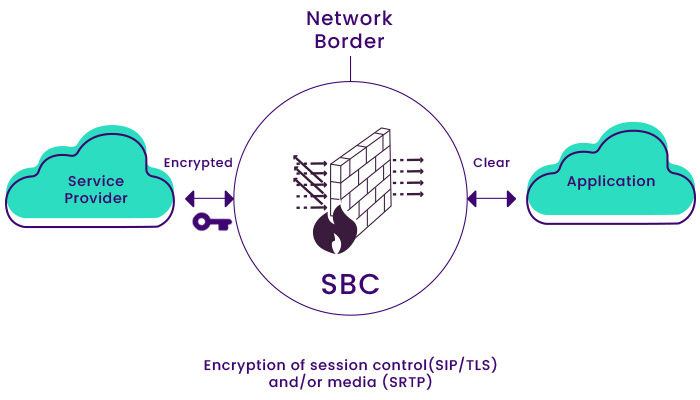
• Encryption of signaling and media messages: It is secured by creating a platform and protects the signaling and media content, IPsec, SRTP, and ZRTP protocols through encryption protocols such as TLS.
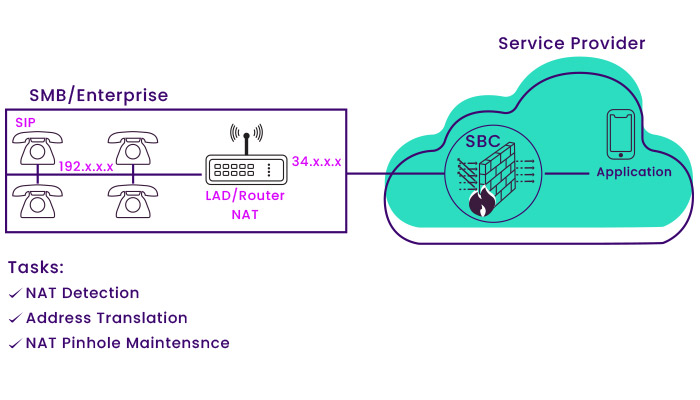
• Check the IP address change of requests or: NAT Traversal The NAT Network Address translation protocol is used to remove the limit on the number of IPv4s in computer networks. Using the NAT protocol does not pose a problem for public access to the Web and email, but it can cause problems for some services, such as VoIP services. In general, NAT Traversal is one of the crucial features of SBCs used in network operators.
The following figure shows all the SBC tasks related to NAT.
• SIP Interoperability: Sometimes, there are differences in the format of messages between VoIP systems of operators and subscribers, so it is necessary to normalize the routing number or even change the SIP header. For this reason, these cases cause the format of the submitted requests to differ from one side to the other; We can conclude that the task of converting messages to standard messages is the responsibility of SBC.
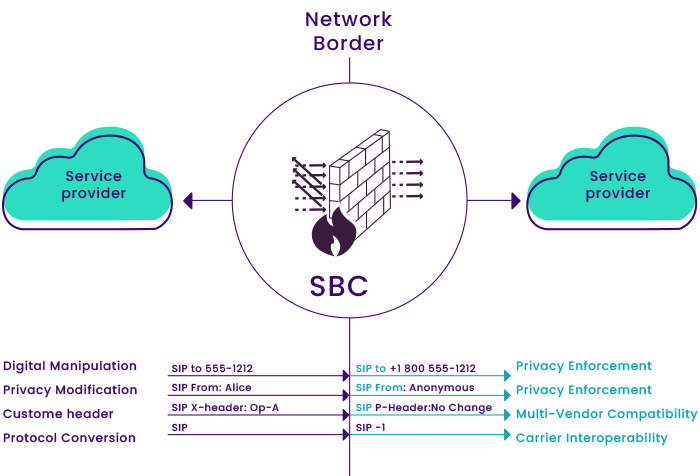
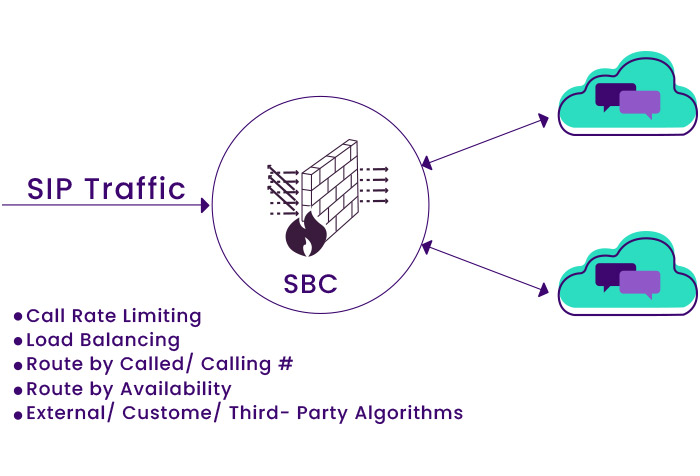
• Routing and traffic management: SBC in the VoIP system is responsible for routing and balancing the traffic load (Load Balancing) traffic sent to the system.
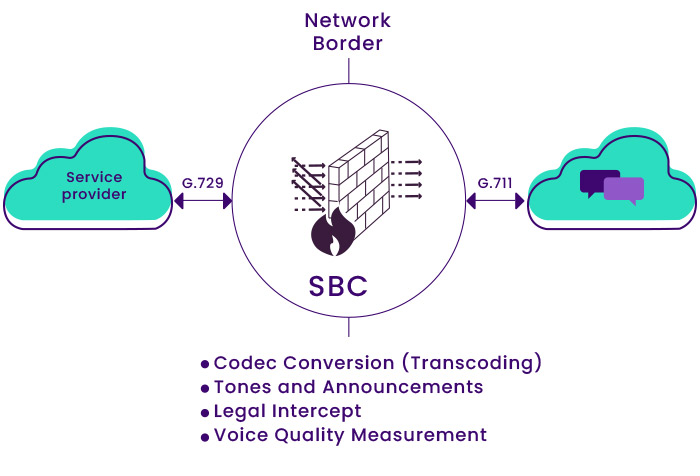
• Convert different media formats to each other: In receiving and sending media between operator-operator or operator-subscriber telephone systems, the formats may differ for some reason. So the task of converting these formats to each other will be the responsibility of SBC.
• Identify and prevent discrepancies in SIP messages: Operators use different vendors of VoIP systems in some cases to send SIP requests with payload and other formats between operators.
• Call recording and measuring call quality: Since all the streams’ content passes through the SBC, it is the best possible place to record calls and measure the quality of SBC communication.
• Legal hearings: If legal and judicial authorities want to prosecute an addressee or a number, they can do so using a secure platform provided by the operator and connecting to the SBC.
How does SBC work?
As mentioned in the SBC Tasks section on VIP systems, in general, SBC performance can be divided into at least four parts:
Security
B2BUA Interoperability
Media Services
Routing or Traffic Management
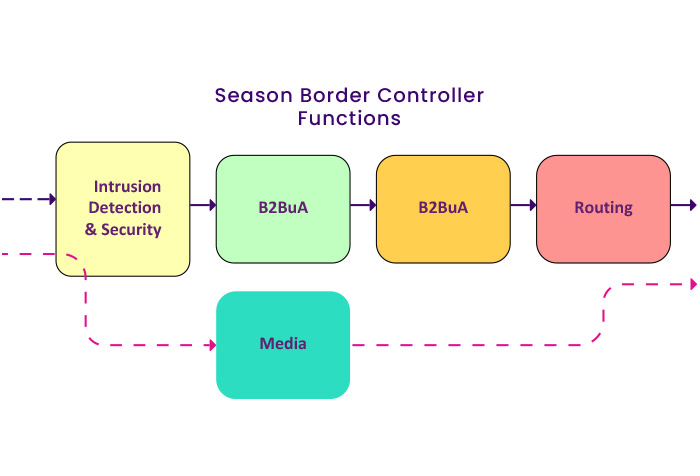
Requests outside the telephone system, which can be to register, make calls, etc., first reach the node (SBC as B2BUA of other components), and this node, if there is no problem, direct it into the system upon request, which then Applies relevant policies such as AAA, charge rolls, etc. Allocates the media path from source to destination so that media does not pass through other telephone system nodes. In the figure above, you can see the schematic of the SBC operation.

